How to Protect Your Site from DDoS Attacks – Before It's Too Late
Published date: 04 April 2025

Introduction: The Growing Threat of DDoS Attacks
In today’s digital landscape, cybersecurity threats are evolving rapidly. Furthermore, Distributed Denial of Service (DDoS) attacks have become increasingly common and sophisticated. These malicious attacks can bring down even the most robust websites within minutes. Consequently, understanding and implementing proper protection measures is no longer optional—it’s essential for survival.
Moreover, DDoS attacks don’t discriminate based on business size. Whether you run a small blog or manage an enterprise website, you’re potentially at risk. Therefore, this comprehensive guide will walk you through everything you need to know about protecting your site from these devastating attacks.
What Exactly Is a DDoS Attack?
Understanding the Basics
A DDoS attack occurs when multiple compromised systems flood your server with overwhelming traffic. Subsequently, your website becomes unavailable to legitimate visitors. Unlike regular traffic spikes, these attacks are intentional and malicious.
Additionally, attackers typically use botnets—networks of infected computers—to launch these assaults. As a result, the attack traffic appears to come from numerous sources simultaneously. Therefore, blocking a single IP address won’t stop the attack.
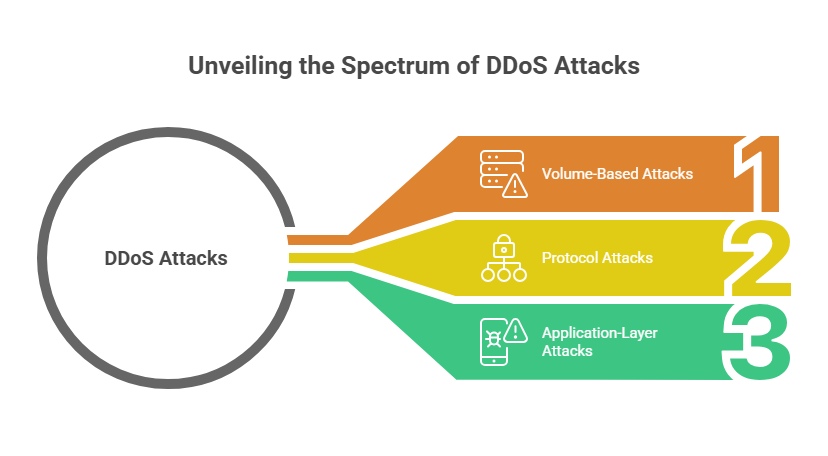
Types of DDoS Attacks You Should Know
Volume-Based Attacks
First and foremost, volume-based attacks aim to consume your bandwidth completely. Indeed, these attacks send massive amounts of data to your server. Consequently, your network becomes saturated and can’t process legitimate requests.
Protocol Attacks
Similarly, protocol attacks exploit weaknesses in network protocols. Moreover, they target server resources rather than bandwidth. Thus, even with available bandwidth, your server can’t respond to requests.
Application Layer Attacks
Furthermore, application-layer attacks are the most sophisticated. They mimic legitimate user behavior, making them harder to detect. Nevertheless, they’re designed to exhaust specific application resources.
Warning Signs: Detecting a DDoS Attack Early
Unusual Traffic Patterns
Firstly, monitor your traffic analytics regularly. Additionally, sudden spikes in traffic from specific geographic locations can indicate an attack. Therefore, establishing baseline metrics is crucial for early detection.
Performance Degradation
Meanwhile, if your website suddenly becomes slow without apparent reason, investigate immediately. Indeed, gradual slowdowns often precede complete outages during DDoS attacks.
Increased Server Resource Usage
Similarly, check your server’s CPU and memory usage frequently. Consequently, unexplained spikes in resource consumption warrant immediate attention.
Essential Protection Strategies
1. Implement a Robust Web Application Firewall (WAF)
A WAF serves as your first line of defense against malicious traffic. Moreover, it filters requests before they reach your server. Consequently, harmful traffic gets blocked automatically.
Benefits of Using a WAF
Furthermore, modern WAFs use machine learning to identify attack patterns. Additionally, they update their rules automatically as new threats emerge. Therefore, your protection stays current without manual intervention.
2. Leverage Content Delivery Networks (CDNs)
CDNs distribute your content across multiple servers worldwide. As a result, they absorb traffic spikes more effectively than single-server setups. Moreover, CDNs provide natural DDoS protection through their distributed architecture.
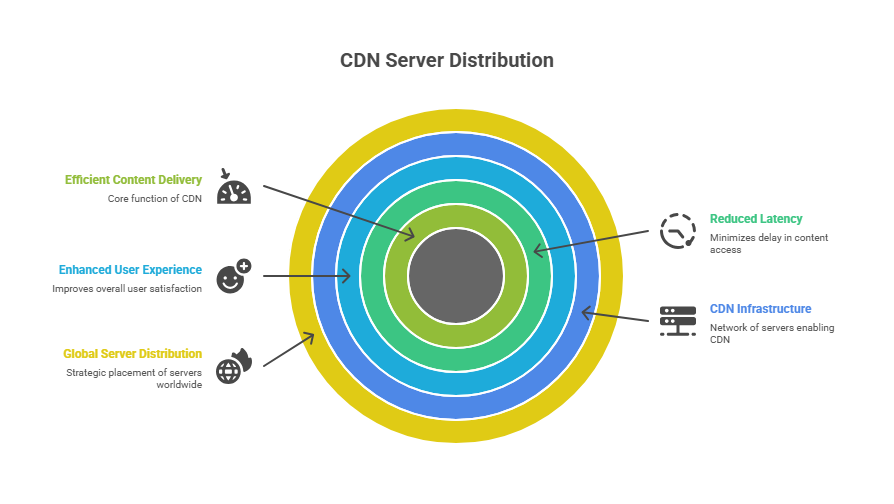
How CDNs Mitigate DDoS Attacks
Firstly, CDNs cache your content on edge servers globally. Subsequently, visitors connect to the nearest server rather than your origin server. Therefore, even during attacks, your main infrastructure remains protected.
Additionally, CDNs can absorb massive traffic volumes that would overwhelm typical servers. Indeed, major CDN providers handle terabits of traffic daily.
3. Configure Advanced Rate Limiting
Rate limiting controls how many requests a single user can make within a timeframe. Consequently, it prevents individual sources from overwhelming your server.
Implementation Best Practices
Moreover, set different limits for various endpoints. For instance, login pages should have stricter limits than static content. Therefore, you balance security with user experience.
Furthermore, implement progressive rate limiting that becomes stricter as suspicious behavior increases. Thus, legitimate users aren’t affected while attacks get blocked.
4. Deploy DDoS-Specific Protection Services
Specialized DDoS protection services offer advanced mitigation capabilities. Additionally, they provide always-on monitoring and automatic response to threats.
Key Features to Look For
Firstly, choose services with large network capacity to absorb volumetric attacks. Similarly, ensure they offer application-layer protection, not just network-layer defense. Moreover, real-time analytics and reporting help you understand attack patterns
5. Optimize Your Server Configuration
Increase Server Resilience
First and foremost, ensure your server has adequate resources. Additionally, implement connection limits and timeout settings appropriately. Therefore, even under stress, your server continues functioning for legitimate users.
Enable SYN Cookies
Furthermore, SYN cookies help prevent SYN flood attacks. These attacks exploit the TCP handshake process. Consequently, enabling this feature adds another protection layer.
6. Implement IP Reputation Filtering
Modern security solutions include IP reputation databases. Moreover, these databases track known malicious IP addresses. Therefore, blocking traffic from these sources prevents many attacks proactively.
7. Use Anycast Network Routing
Anycast routing distributes traffic across multiple servers automatically. Subsequently, even if one server gets overwhelmed, others continue serving content. Indeed, this approach significantly improves resilience against DDoS attacks.
8. Establish Redundancy and Failover Systems
Additionally, maintain backup servers in different locations. Consequently, if your primary server goes down, traffic automatically redirects to backups. Therefore, your website remains accessible even during severe attacks.
Advanced Protection Techniques
Traffic Analysis and Behavioral Patterns
Furthermore, implement systems that learn normal traffic patterns. Subsequently, they can identify anomalies indicating potential attacks. Thus, you get early warnings before attacks cause significant damage.
Geographic Blocking When Appropriate
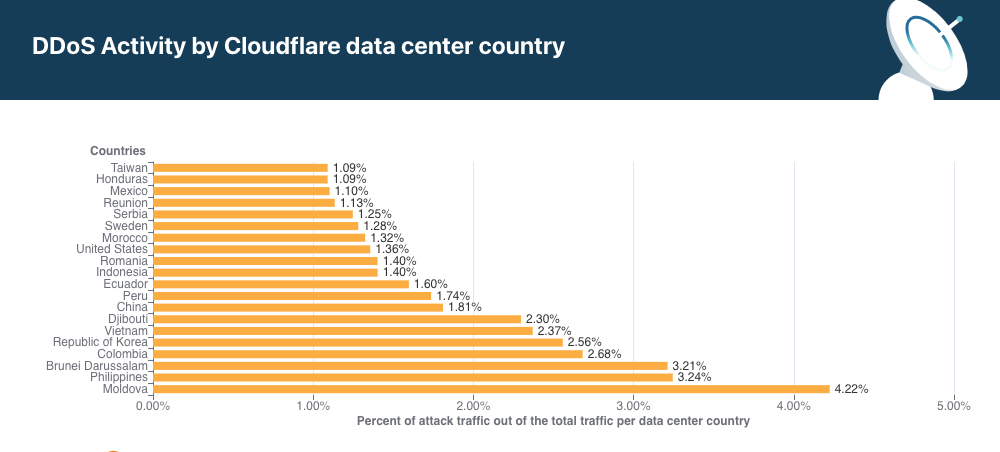
If your business operates in specific regions, consider blocking traffic from irrelevant locations. However, use this carefully to avoid blocking legitimate international users.
Regular Security Audits
Moreover, conduct quarterly security assessments of your infrastructure. Additionally, penetration testing helps identify vulnerabilities before attackers exploit them.
Creating an Incident Response Plan
Before an Attack Occurs
Firstly, document your response procedures clearly. Additionally, assign specific roles and responsibilities to team members. Therefore, everyone knows their tasks during an emergency.
During an Attack
Meanwhile, follow your documented procedures systematically. Furthermore, communicate with your hosting provider and security services immediately. Thus, you coordinate responses effectively.
After an Attack
Subsequently, conduct thorough post-incident analysis. Moreover, identify what worked and what needs improvement. Therefore, you strengthen your defenses for future incidents.
Monitoring and Maintenance
Continuous Monitoring Is Essential
Implement 24/7 monitoring of your website and server resources. Additionally, set up alerts for unusual activity. Consequently, you can respond to threats immediately, regardless of when they occur.
Regular Updates and Patches
Furthermore, keep all software, plugins, and themes updated consistently. Indeed, outdated software contains vulnerabilities that attackers exploit readily. Therefore, enable automatic updates whenever possible.
Performance Baseline Establishment
Moreover, document your website’s normal performance metrics. Subsequently, deviations from these baselines help identify potential issues quickly.
Cost Considerations and ROI
Investment in Protection Pays Off
While security solutions require investment, recovery from successful attacks costs significantly more. Additionally, consider reputation damage and lost revenue during downtime. Therefore, adequate protection delivers strong return on investment.
Scalable Solutions for Every Budget
Furthermore, protection options exist for all budget levels. Start with basic measures and scale up as your site grows. Indeed, even free CDN tiers offer substantial protection.
Legal and Compliance Aspects
Understanding Your Responsibilities
Moreover, depending on your industry, you might have legal obligations regarding security. Additionally, GDPR and similar regulations require protecting user data adequately. Therefore, DDoS protection becomes a compliance necessity, not just best practice.
Future-Proofing Your Defense Strategy
Staying Ahead of Evolving Threats
Attack methods constantly evolve, so your defenses must too. Furthermore, follow cybersecurity news and update your strategies accordingly. Additionally, participate in security communities to learn from others’ experiences.
Artificial Intelligence and Machine Learning
Moreover, next-generation protection systems increasingly use AI for threat detection. These systems identify complex attack patterns that traditional methods miss. Therefore, consider solutions incorporating these technologies.
Conclusion: Act Now to Protect Your Digital Assets
DDoS attacks represent serious threats to online businesses everywhere. However, with proper preparation and robust protection measures, you can significantly reduce your vulnerability. Furthermore, the strategies outlined in this guide provide comprehensive defense against various attack types.
Remember, reactive approaches cost more than proactive protection. Therefore, implement these measures before experiencing an attack. Additionally, regularly review and update your security posture as threats evolve.
Finally, don’t tackle this alone. Leverage professional security services, consult with experts, and stay informed about emerging threats. Consequently, you’ll maintain a secure, reliable online presence that users can trust.
Take action today—your website’s security depends on it. Moreover, the time and resources you invest now will pay dividends by preventing costly downtime and reputation damage later.