10 Best Free Screen Recorder for PC in 2025 (Complete Guide)
10 Best Free Screen Recorder for PC in 2025 (Complete Guide) Screen recording is no longer something only gamers or YouTubers do.…
Read More →
10 Best Free Screen Recorder for PC in 2025 (Complete Guide) Screen recording is no longer something only gamers or YouTubers do.…
Read More →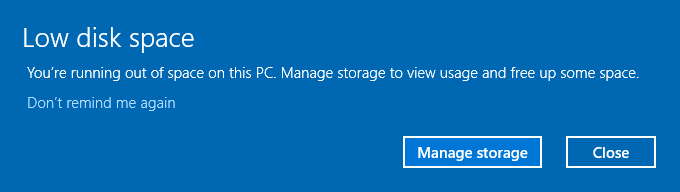
Why You Lose Storage After a System Upgrade (Explained Simply) Have you ever upgraded your device or operating system, only to find…
Read More →
NTLMv1: The Outdated Authentication Protocol You Should Retire Image source: Redlings In today’s cybersecurity landscape, legacy protocols like NTLMv1 represent serious vulnerabilities.…
Read More →
Kerberos vs NTLM: The Complete Guide to Windows Authentication Protocols In the world of Windows-based authentication, two protocols have dominated for decades:…
Read More →
Veeam Data Cloud vs Veeam Backup: The Complete Comparison Guide In today’s data-driven world, backup solutions are no longer optional – they’re…
Read More →
Understanding Computer Networks: A Comprehensive Guide In today’s digital world, computer networks play a crucial role in connecting devices, enabling communication, and…
Read More →
Quantum Computing in 2025: The Next Tech Revolution Explained Simply Introduction Imagine a computer so powerful it could solve in seconds what would take…
Read More →SPF Explained: Your Email’s Security Bouncer (Simple Guide for Everyone) Imagine your email inbox as an exclusive nightclub. SPF is like the…
Read More →
Single Sign-On (SSO) Explained: The Key to Secure & Hassle-Free Logins Tired of remembering dozens of passwords? Frustrated with constant login prompts? Single…
Read More →
5 Major Reasons to Ditch HDDs or SSDs and NVMe in 2025 If your computer still uses an old Hard Disk Drive (HDD),…
Read More →